
On March 2nd 2021, Microsoft released security patches for seven bugs affecting Microsoft Exchange Servers. Four of these bugs are zero-day exploits being used to attack on-premises versions of Microsoft Exchange servers.
Zero day vulnerabilities affecting Microsoft Exchange Servers
The vulnerabilities affect Microsoft Exchange Server 2010, 2013, 2016, and 2019 (Exchange Online is not affected). In most cases, attackers are dropping an ‘eval’ webshell onto the vulnerable servers – these are more commonly referred to as ‘choppers’ or ‘China choppers.’ With this foothold, attackers are then able to perform remote code execution (RCE) and compromise credentials.
Microsoft Threat Intelligence Centre (MSTIC) confidently attributes this campaign to HAFNIUM, “a group assessed to be state-sponsored and operating out of China, based on observed victimology, tactics and procedures.” [1]
Recommendations
We understand that there is already a lot of information out there about these vulnerabilities, the attack details and corresponding recommendations. Now that the vulnerabilities are publicly and widely disclosed, it essential that all our customers act swiftly and cautiously. Other nation-state actors and criminal groups will not hesitate to exploit unpatched systems.
In line with Microsoft’s recommendations, we encourage our clients running Microsoft Exchange servers to patch these vulnerabilities as soon as possible.
Microsoft has provided a script for clients to get a quick inventory of the patch-level status on on-premises Exchange servers and to check for HAFNIUM Indicators of Compromise (IOCs): https://github.com/microsoft/CSS-Exchange/tree/main/Security
What are the next steps?
Content Security’s Lead Investigator Grant Haroway notes that even if results are returned for the CVE-2021-26855 vulnerability, further investigation is required to determine if the attempts were successful:
“Analysis shows that successful exploitation requires the use of a legitimate email address. If results are found using the Microsoft supplied script for [CVE-2021-26855], review the events in detail to determine if a legitimate email was utilised.”
1. Search for CVE-2021-26855 exploit attempts:
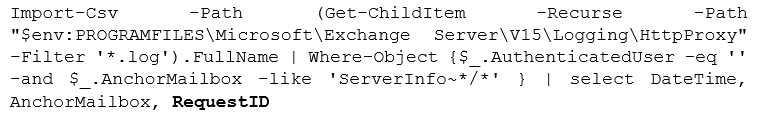
2. Crosscheck logs using resulting RequestIDs (replace xxxx with returned RequestIDs):
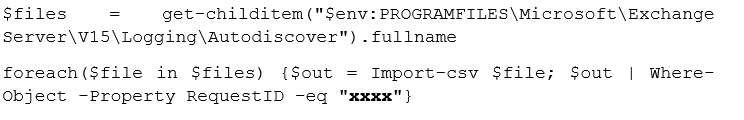
3. Review the following fields:
- GenericInfo for email used in the attempt:
o … [email protected] … - GenericErrors for result:
o e.g. “message=The email address can’t be found.;”
About HAFNIUM
HAFNIUM is a network of hackers that targets organisations across a wide number of verticals, including health and infectious disease researchers, defence, law, higher education, NGOs and think tanks.
Microsoft has provided the following details to assist customers with understanding the techniques used by HAFNIUM to exploit these vulnerabilities:
- CVE-2021-26855 is a server-side request forgery (SSRF) vulnerability in Exchange that allows the attacker to send arbitrary HTTP requests and authenticate as the Exchange server. According to researchers, this vulnerability allows attackers to steal the full contents of users mailboxes. [2]
- CVE-2021-26857 is an insecure deserialization vulnerability in the Unified Messaging service. Insecure deserialization is where untrusted user-controllable data is deserialized by a program. Exploiting this vulnerability gives attackers the ability to run code as SYSTEM on the Exchange server. This requires administrator permission or another vulnerability to exploit.
- CVE-2021-26858 and CVE-2021-27065 are post-authentication arbitrary file write vulnerabilities in Exchange. If attackers can authenticate with the Exchange server then they can use this vulnerability to write a file to any path on the server. They can authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials.
References
For more information please contact our cybersecurity professionals today.
Recent news
Latest posts
Key Strategies and Best Practices for Enhancing OT Security
05 April, 2024A Comprehensive Guide to Third Party Risk Management (TPRM)
26 February, 2024









