
Ransomware, phishing & compromised credentials: perpetual cyber security hurdles
The Office of the Australian Information Commissioner’s (OAIC) most recent Notifiable Data Breach (NDB) report reveals that phishing, ransomware and compromised credentials remain the top successful vectors for attack. How are businesses to regularly protect against these persistent cyber security threats?
Report overview
The OAIC’s January to June 2021 NDB report showed an overall decrease of 16% in breach notifications compared to the July to December 2020 period. As per usual, malicious attacks were the leading source of data breaches (65%), followed by human error (30%) and system fault (5%).
After three years of the NDB report, it is no surprise that health service providers reported the highest number of breaches, accounting for approximately one fifth of all notifications. Finance notified 13% of all breaches, and the Australian Government remained in the top five industry sectors for the second consecutive report, with approximately 7% of notifications.
Breach sources
While the breakdown of breach source varied across each industry sector, 66% of criminal attacks were the result of cyber incidents and 34% could be owed to rogue employees, social engineering/impersonation, and theft of paperwork.
Over half of cyber incidents involved external threat actors gaining access to accounts using compromised or stolen credentials, with email-based phishing increasing by 5% in the last reporting period:
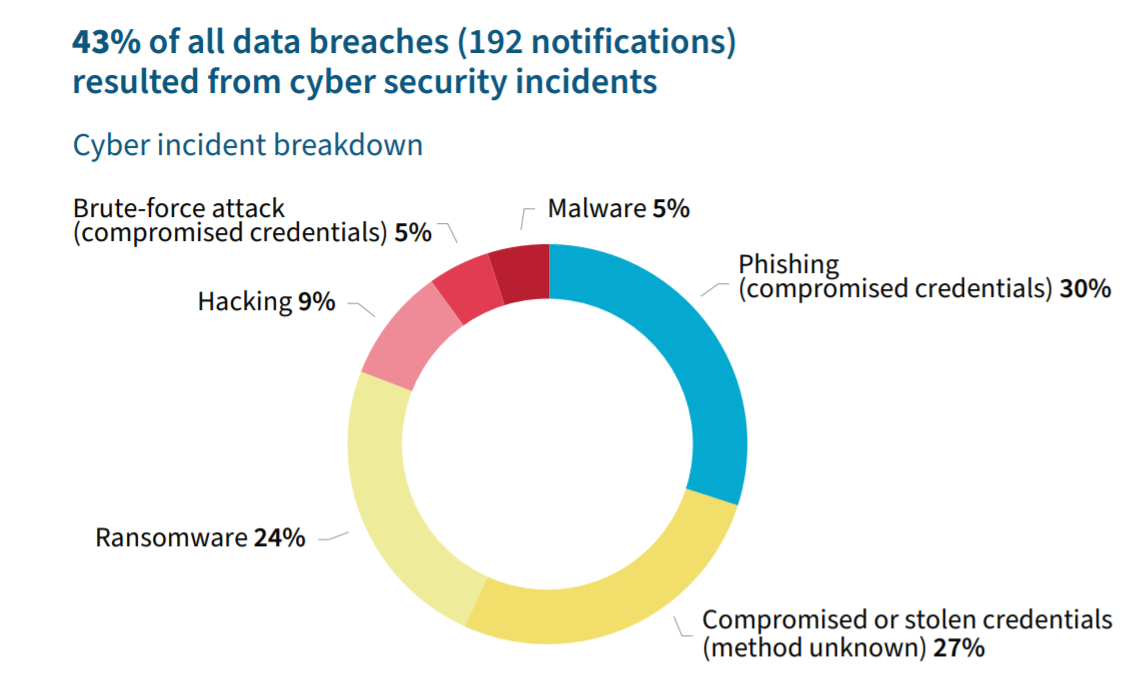
Figure 1. cyber incident breakdown – all sectors, oaic notifiable data breach report january-june 2021
Unfortunately, phishing, compromised credentials and ransomware are here to stay
With great results yielded for cyber attackers, it’s evident that these threat vectors will be perpetual mountains to climb for years to come. We’ve seen them cripple businesses time and time again, and it’s time to recognise that these are chronic, long-lasting issues that call for continuous protection.
What the NDB report shows us is that having the right controls in place is nothing without having the right knowledge to back it up. While malicious incidents consistently comprise the majority of breaches in the reports, the role human error plays in both criminal attacks and internal breaches should not be downplayed.
As Australian Information Commissioner and Privacy Commissioner Angelene Falk reminds us, ‘human error remains a major source of data breaches. Let’s not forget the human factor plays a role in many [malicious] cyber security incidents, with phishing being a good example.’
Phishing, compromised credentials and ransomware are not mutually exclusive
As Proofpoint’s 2021 State of the Phish Report shows, successful phishing attacks lead to more than just data loss – the results are more often than not ransomware, credential compromise and other malware infection:
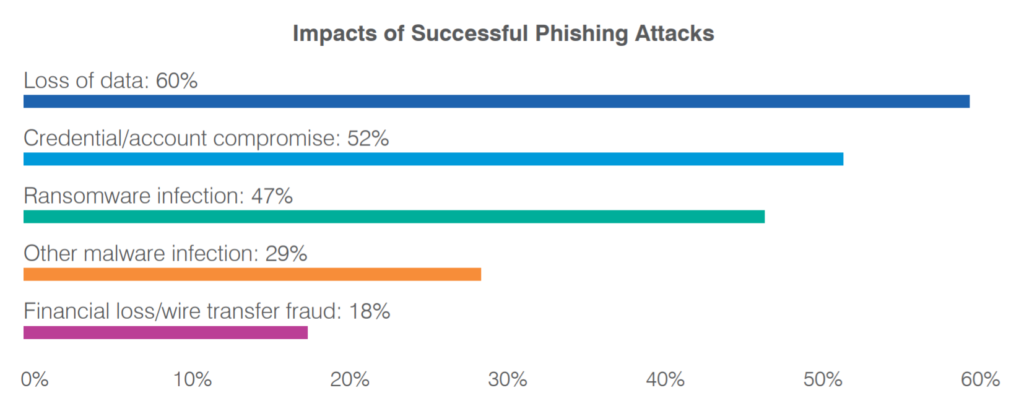
FIGURE 2. IMPACTS OF SUCCESSFUL PHISHING ATTACKS, PROOFPOINT 2021 STATE OF THE PHISH REPORT
If nothing else, this truly emphasises the need for greater staff security awareness training, with a focus on phishing, as well as:
- Reporting and escalating fraud;
- Data protection measures;
- Avoiding malicious attachments and links; and
- Protecting user credentials.
How to jump these perpetual cyber security hurdles?
Security awareness is still one of the most effective countermeasures to preventing breaches from these three attack methods, with 80% of organisations owing a reduction in phishing susceptibility to information security awareness training (ISAT). It is a critical layer of defence-in-depth, helping businesses bolster awareness and therefore protection against phishing, ransomware, malware, and more.
Whether in an ad-hoc or managed capacity, businesses should undertake ISAT to increase staff knowledge and vigilance, particularly around the four areas of focus above. Businesses that implement ISAT equip their people with the right tools and skills to adequately defend against cyber attackers, minimising breaches from both malicious vectors and internal faults.
Content Security’s Cyber Security Awareness Training
We’ve developed a Managed Cybersecurity Awareness Program (MCAP) to help businesses promote a culture of awareness and protect their data. To discuss your ISAT needs, please contact our consultants today.
About the report
For more information please contact our cybersecurity professionals today.
Recent news
Latest posts
Key Strategies and Best Practices for Enhancing OT Security
05 April, 2024A Comprehensive Guide to Third Party Risk Management (TPRM)
26 February, 2024









