
Identity Governance and Administration (IGA) is an important aspect of managing and protecting an organization’s digital assets and resources. Essentially, IGA involves establishing and enforcing policies and procedures for controlling access to systems and data, as well as monitoring and reporting on user activity. IGA also enables organizations to increase organisational efficiency and agility through automation and intuitive workflows.
In the current landscape, organizations of all sizes and industries are becoming more and more reliant on a hybrid workforce. As a result, it’s more important than ever to ensure that access to systems and data is carefully managed and secured. However, as users can access systems from any location and any device, effective identity and access management has become increasingly challenging. In this article, we’ll highlight the importance of implementing an IGA solution for your organization.
What are the key components of an IGA solution?
Identity Governance and Administration solutions provide businesses with the tools to effectively manage identity and access for its users. Specifically, IGA does this through:
- Identity management
An IGA solution allows IT teams to create, maintain, and manage user identities within an organization. It includes creating new user accounts, updating existing ones, and disabling or deleting accounts that are no longer needed. By implementing IGA, organisations can streamline approvals.
- Access management
This involves controlling and monitoring access to resources based on the user’s role, responsibilities, and clearance level. It includes granting, revoking, and modifying access permissions. With tools such as ‘Just-In-Time’ Access and access from anywhere, IGA provides frictionless access for your users.
- Compliance
An IGA solution ensures that an organization’s access management policies and procedures comply with applicable laws, regulations, and industry standards. It includes regular audits and reporting to ensure compliance with the relevant standards. IGA empowers organisations to have total control over Governance Automation & Management.
Benefits of IGA
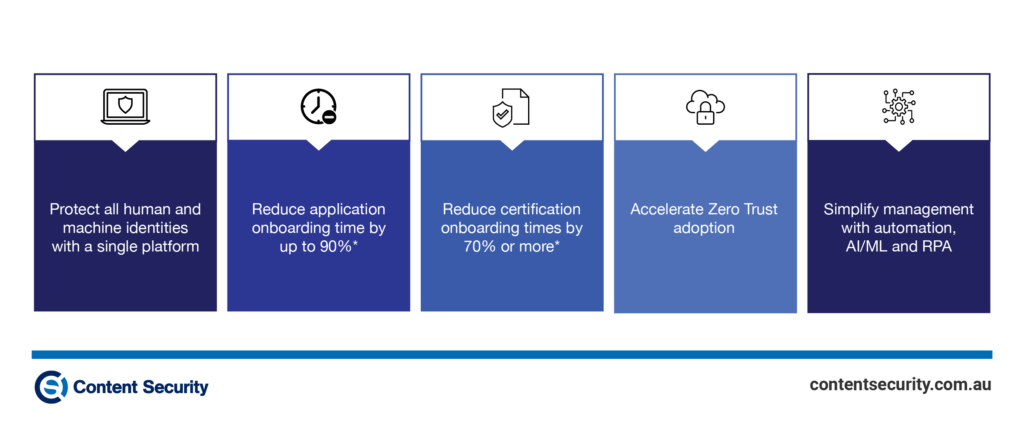
- By streamlining decisions, IGA empowers business to protect all human and machine identities with a single platform. IGA ensures that only authorized individuals have access to the systems and resources they need to do their jobs, and that their access is appropriately restricted based on their role and responsibilities.
- By Simplifying Deployment and Management, effective IGA solutions can reduce application onboarding times by up to 90%.
- With IGA, business managers, application owners and role owners, can make informed decisions about access certifications, as well as automate processes to increase owner engagement, speed decisions, and reduce enterprise risk.
- In a previous blog post, You’re verifying everything and trusting nothing – now what? , we discussed the growing need for organisations to adopt Zero Trust. Implementing an IGA solution accelerates this adoption by providing complete visibility for both Human and IoT identities.
Common IGA Misconceptions
1. IGA is only about Access Control: While Access Control is a key component of IGA, it also includes Identity Management and Compliance. It involves creating, maintaining, and managing user identities, controlling and monitoring access to resources, and ensuring compliance with the relevant laws, regulations, and industry standards.
2. IGA is only for large organizations: While large organizations may have more complex access management needs, IGA can benefit organizations of any size. Even small organizations can benefit from the automation, improved security and compliance that is achieved through IGA.
3. IGA is only about technology: While technology is an important component of IGA, it is not the only aspect. IGA also involves defining policies and procedures, identifying key stakeholders, and ongoing monitoring and maintenance.
4. IGA is a one-time process: Implementing IGA is not a one-time process, it requires ongoing monitoring and maintenance to ensure that the system is functioning properly and that all access permissions are up-to-date.
Effective Identity Governance and Administration is critical for ensuring the security and integrity of an organization’s systems and data. It helps to protect against unauthorized access and misuse, while also enabling employees to access the resources they need to do their jobs effectively. If you’re responsible for managing IGA in your organization, it’s important to stay up-to-date on best practices and industry standards to ensure that your policies and procedures are effective and efficient.
For more information please contact our cybersecurity professionals today.
Recent news
Latest posts
Key Strategies and Best Practices for Enhancing OT Security
05 April, 2024A Comprehensive Guide to Third Party Risk Management (TPRM)
26 February, 2024









