Zero Trust is not a singular technology implementation, nor is it a service that can be purchased at any point in time. Zero Trust is an ongoing strategy, premised on the notions that users and/or devices cannot be implicitly trusted, that they must always be verified, and that breaches are always assumed to happen.
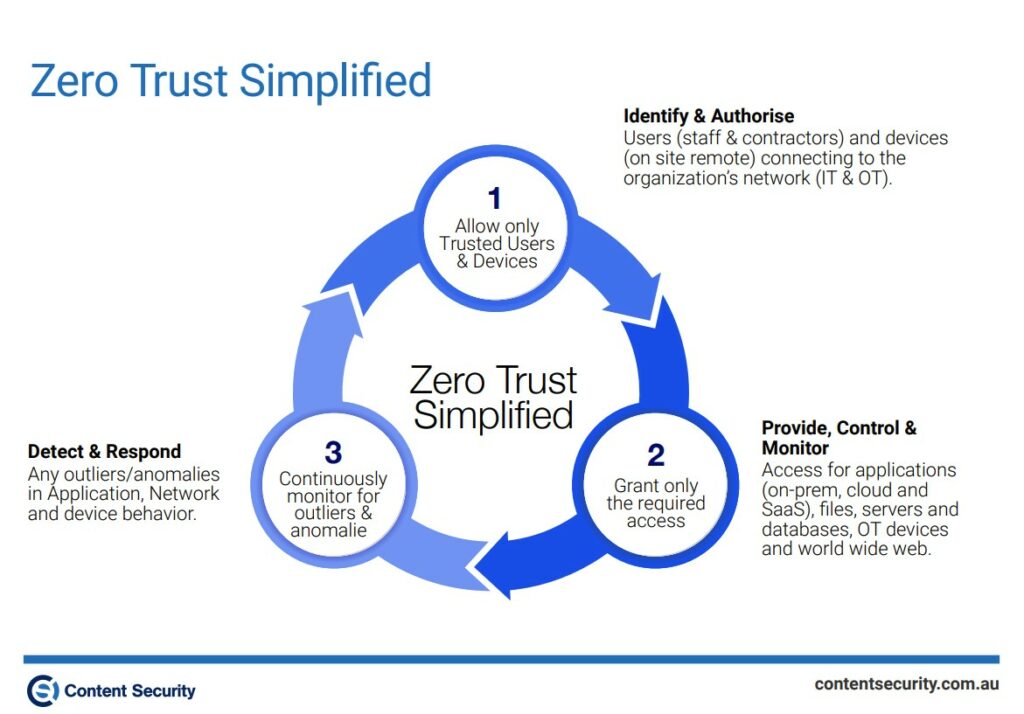
In our previous blog posts, we covered this approach in our recent blog on Identity and Access Management, where organizations must only allow trusted users and devices access. In our post on the Control and Monitor stage, we ensured that each request is verified and only the appropriate access is granted to these trusted users and devices. Now that your organization trusts nothing and verifies everything, what’s next?
In this article, we will explore how organizations can practice the third stage of the Zero Trust Model – Detecting and Responding to anomalies by implementing an “assume breach” mindset.
What is the third stage of the Zero Trust model?
Zero Trust is an approach that assumes a breach is inevitable and that an advanced persistent threat (APT) is certain to happen. In IBM’s Data Breach Report 2022, – 83% of organisations have had more than one data breach. As such, organisations must implement an “assume breach” mindset, in which controls are put in place for detecting and responding to potential threats.
Detect and Respond is a continually evolving aspect of Zero Trust, enabling organisations to monitor network traffic for suspicious activity or malicious threat actors. Any outliers in application, network, user, and device behaviour can be caught quickly and ensure teams respond in a timely and well-practiced manner. From hackers to nation-states, organisations have a greater chance of halting or remediating threats before they cause deeper damage.
Keys for building an assume breach mindset:
- Minimizing blast radius.
- Segmenting access.
- Verifying end-to-end encryption.
- Utilising analytics to gain deep visibility.
Why are detection and response important?
In an increasingly complex threat landscape, perimeter-based security is becoming more and more ineffective. With the proliferation of hybrid work models and sophisticated advanced persistent threats, verifying users is simply not enough to be cyber secure. By implementing a model that revolves around the continuous monitoring of anomalies, organisations can effectively mitigate the impact and severity of cyberattacks. They can do this through the following:
- Minimizing attack surfaces to create granular subsets within a network, ensuring users or devices can only connect to or access the resources and services that are relevant and needed.
- Reducing time and cost of responding to and cleaning up after a breach. IBM’s Data breach report has revealed that organizations with zero trust deployed saved on average, USD 1 million in breach costs compared to organizations without zero trust deployed.
- Greater visibility from administrator to executive levels. visibility is essential to both detecting and responding to threats, as well as blocking any undesired events across your organization.
As opposed to traditional security models, Zero Trust asks organisations to reduce risk first before validating the user/device. Implementing an assume breach mindset ensures that cybersecurity teams remain vigilant in both the detection and responding of threats.
How to implement an assume breach mindset?
Implementing an assume breach mentality often happens in layers. Whilst the toughest challenge is shifting the mindset of the security team, below are a few security controls that aid in both threat detection and response.
SIEM – (Traditional Approach)
- Visibility is critical in implementing a Zero trust environment. A well-designed SIEM ensures the continuous collection of log data and garners deep visibility within the environment.
SOC – Once organizations have visibility into the environment, continuous monitoring is essential in improving and maturing their Zero Trust Strategy. SOC provides this audit function and assists security teams respond to any threats efficiently.
EDR, MDR or XDR (Advanced Approach)
- EDR: Allows security teams to detect and respond to threats on the endpoints.
- MDR: Serviced management of endpoint security, identifies and limits the impact of threat actors.
- XDR: Allows security teams to detect and respond to threats, whilst also increasing visibility.
Web Application Firewalls
- Enable the continuous monitoring of threat vectors through micro-segmentation.
Vulnerability & Patch Management
- Allows teams to detect and respond to any potential threats.
Penetration tests/red teaming exercises
- Validates the posture of an organisation’s security and infrastructure, whilst also flagging any room for improvements.
Implementing an assume breach mindset doesn’t require all the above security controls. Instead, the right mix can enable security teams to deliver Zero Trust Architecture.
For more information please contact our cybersecurity professionals today.
Recent news
Latest posts
Key Strategies and Best Practices for Enhancing OT Security
05 April, 2024A Comprehensive Guide to Third Party Risk Management (TPRM)
26 February, 2024










